The problem with traditional office networks is that they allow far too much Internet access from computers with important information. Most office “Firewalls” are configured to prevent incoming traffic that is not requested by computers within the office, but they allow outgoing traffic.
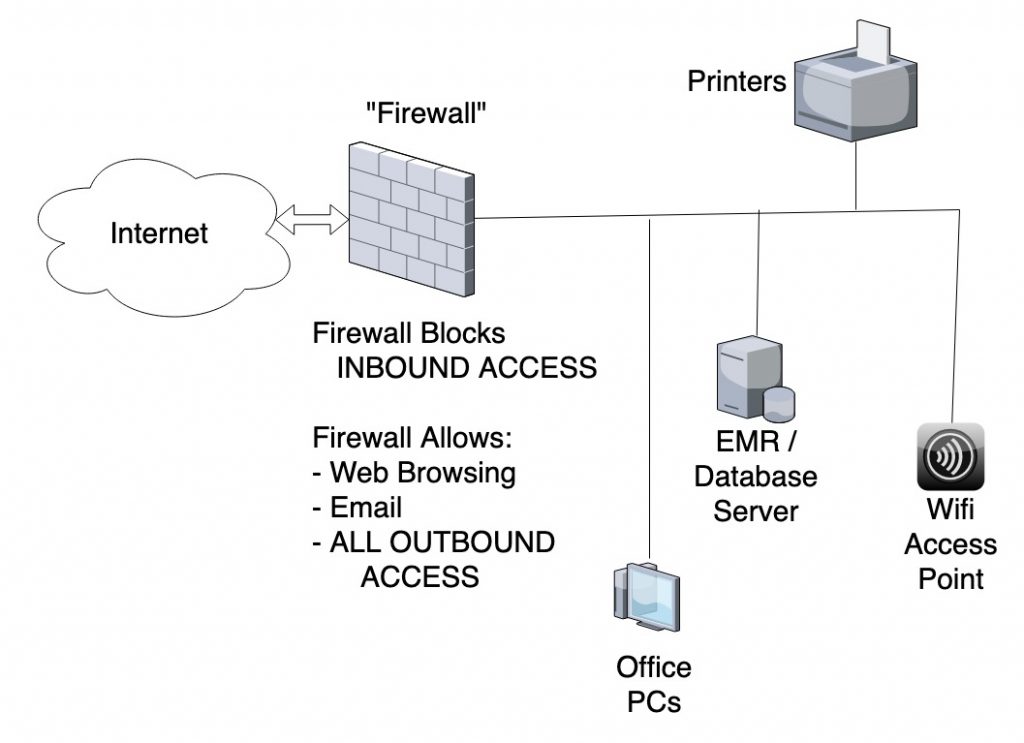
This shows how most office networks are designed by the IT Professionals who configure them.
The problem is that this Firewall may prevent incoming attacks, but does nothing to protect against the most common types of attacks: email attachments, websites, and social engineering.
It is important to protect against incoming attacks, but that is pretty easy (although also easy to get wrong, such as by leaving ingress ports open and not updating security software to the latest versions). However, because it is relatively easy to block incoming attacks, most attackers use outbound connections to attack the network.
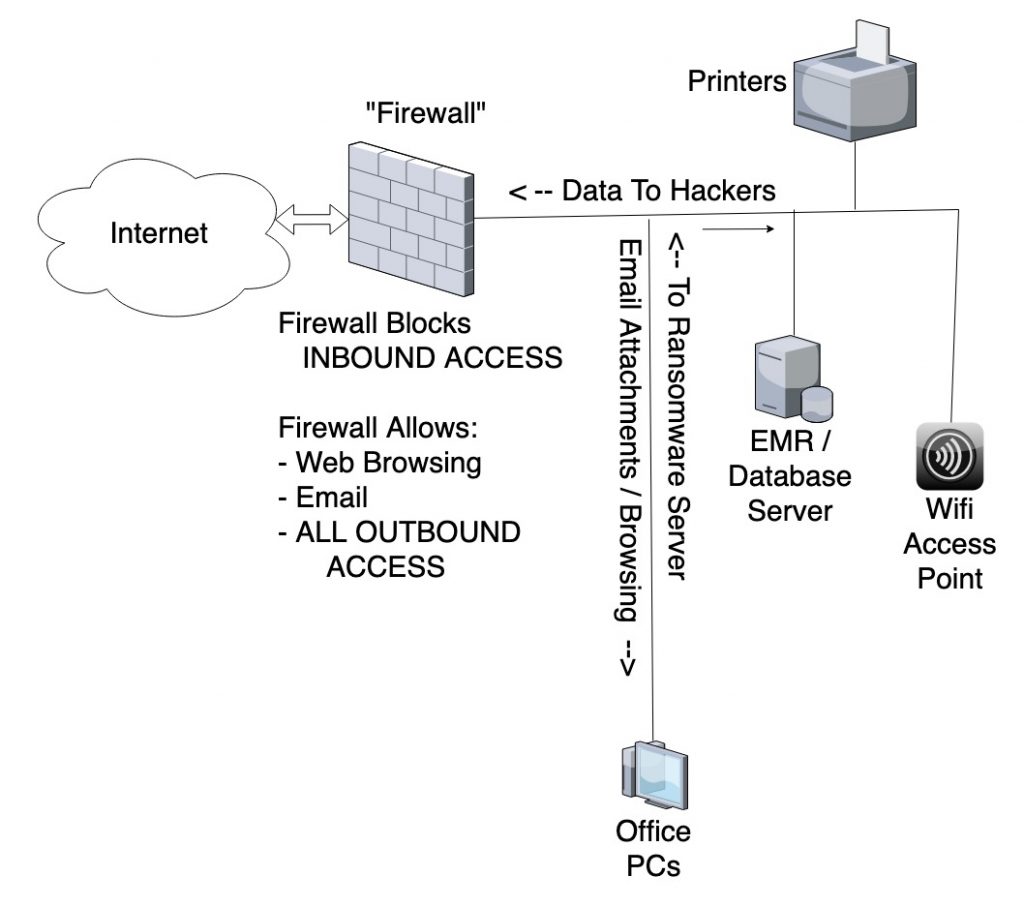
How do they initiate outbound connections from within a private network they do not control? The most common methods are (1) email attachments and (2) compromised websites. Email attachments are the easiest: just send an email to someone in the office with software attached.
This works best when combined with social engineering: for example, use a forged “From” address of someone else in the company, include language like “please pay the attached invoice,” or an inflammatory subject line like “is that you in this photo?!?”
Once someone opens the attachment or goes to the website (either downloading something from the website or with a security defect in the browser), the software starts running on the Office PC, with access to the EMR/Database server. It also connects to the outside world through the Firewall (which, remember, always allows outgoing connections in the traditional office network configuration) to upload your private data and/or ransomware passwords to the Hacker’s computers.