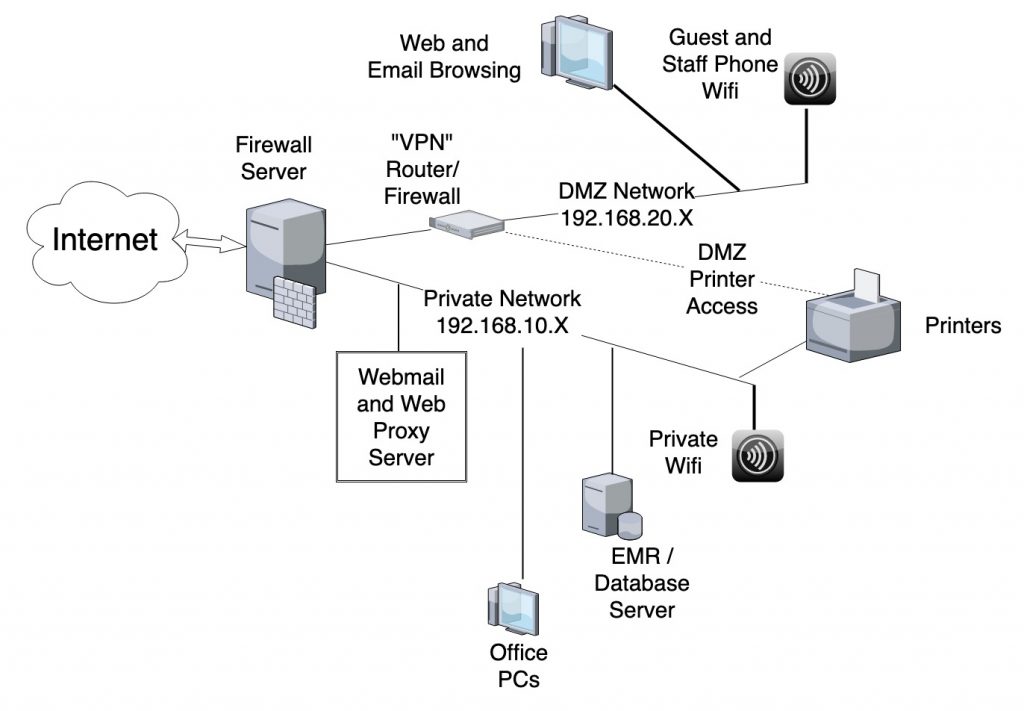
Two Private Networks
The overall design uses a PC running Linux with multiple ethernet ports to run the Firewall and manage overall network configuration. This also allows a single source for DHCP, DNS, and Time services.
The Private Network, shown as 192.168.10.X in the diagram, includes all of the Office PCs that can access any internal information of the practice, including EMR and Practice Management systems. It can also include a Webmail and/or Web Proxy Server, which is allowed to access the Internet and which limits the external information that can be made available to the Office PCs.
The “DMZ” Network, shown as 192.168.20.X in the diagram, allows staff to use systems to access anything on the Internet that they need, but does not provide access to any private information on the Private Network.
A separate router is used to physically separate this network from the Private Network, but this configuration shows the DMZ Network being connected to the main Firewall, to allow pinpoint access, such as to allow printing on the office printers from the systems on the DMZ Network.
Another, arguably stronger, configuration would completely separate the DMZ Network from the main Firewall, but that would not allow DMZ Network systems to print on office printers without allowing similar access from the Internet. Of course, you could always put some printers into the DMZ.
The DMZ Network also has the Access Point with Wifi networks for guests in the office and also for staff mobile phones, so that traffic from those cannot compromise the Private Network.
Firewall Server
The Firewall Server is simply a PC with multiple ethernet ports that runs the open-source Linux operating system. Linux allows the Firewall Server to control and route traffic according to the Firewall rules, and also allows the Firewall Server to run services such as Dynamic Host Configuration Protocol (DHCP) to assign IP addresses to individual systems, Domain Name Service (DNS) to allow systems in the office to connect without making requests to the Internet, and Network Time Protocol (NTP) to provide a common time source for systems in the office.
A CRITICAL FEATURE OF THE FIREWALL IS THAT IT BLOCKS ALMOST ALL OUTGOING AS WELL AS INCOMING CONNECTIVITY. Although this is clearly a reduction in capability and convenience from inside the Private Network, it is required to prevent the common breaches mediated by Email attachments and Web browsing.
There are several free open-source versions of Linux that will work, but my favorite is Ubuntu Server LTS. “LTS” means “Long Term Support,” and reflects the promise of Ubuntu to provide security updates to Ubuntu Server LTS systems for five years from its original release. Ubuntu releases a Server LTS version in April every other year, named by the year and the month. Ubuntu Server LTS 18.04 is released in April 2018, and Ubuntu Server LTS 20.04 is released in April 2020.
Ubuntu can be used not only for the Firewall server, but for other Linux servers in the office, such as the Webmail and/or Web Proxy Server. However, many EMR and Practice Management systems will require proprietary servers such as Windows Server and/or SQL Server (although SQL Server can now run on Linux as well).
“VPN” Router Firewall
This is not a VPN (Virtual Private Network), but a VPN Router is a very capable device with multiple other abilities. This is essentially a small computer with multiple ethernet connections running software for network configuration. It provides isolation between the DMZ Network and the rest of the system. The router I use is a TP-Link TL-R6000VPN, available on Amazon for under $60.
Webmail and/or Web Proxy Server
This is an optional component that allows improved communication capabilities from the Office PCs on the Private Network. Because the Firewall prevents almost all outgoing access from the Office PCs on the Private Network, those PCs will have no access to outside web systems, such as Brilliant Distinctions or My Med Leads. One perfectly good solution is to use the PCs on the DMZ network to access those systems; in that case there would be no need for a Webmail and/or Web Proxy Server.
However, for the Office PCs to be able to access specific whitelisted websites, such as Brilliant Distinctions or My Med Leads, or to view and send emails without access to the dangerous attachments, these services can be provided. These are services that run on a Linux PC, not necessarily separate physical “Servers.”
The Webmail Server runs software such as open-source Roundcube, which typically runs on a server somewhere so you can access your email using a browser. However, this Webmail Server is modified to not allow downloading of email attachments, so that systems using it can view and send emails, but not be affected by email attachments. The Webmail Server is permitted to access the Internet through the Firewall to an IMAP Service that actually hosts the email. There are several choices, although I have used Pair Networks. Even their most inexpensive Shared Hosting plans include IMAP Email Services. You can get a 20% reduction of your first Pair bill by using code pairref-JwfgjsvE
The Web Proxy Server runs software such as open-source Squid. The browsers on the Office PCs are configured to use this system as their Internet Proxy, which means that any requests to browse are directed to the Web Proxy Server (since the Firewall prevents direct access to the Internet from those PCs).
Those browsing requests are inspected by the Web Proxy Server to see if they access whitelisted websites or not. If not, the Web Proxy Server shows a page on the browser that says Sorry, you are not authorized to access that website. However, if the request is for a whitelisted site, the Web Proxy Server passes the request onto that site through the Firewall and returns the response to the browser. This works even with encrypted https connections because the connection occurs before encryption, and the actual communication between the browser and the outside Internet server remains encrypted between those two systems.