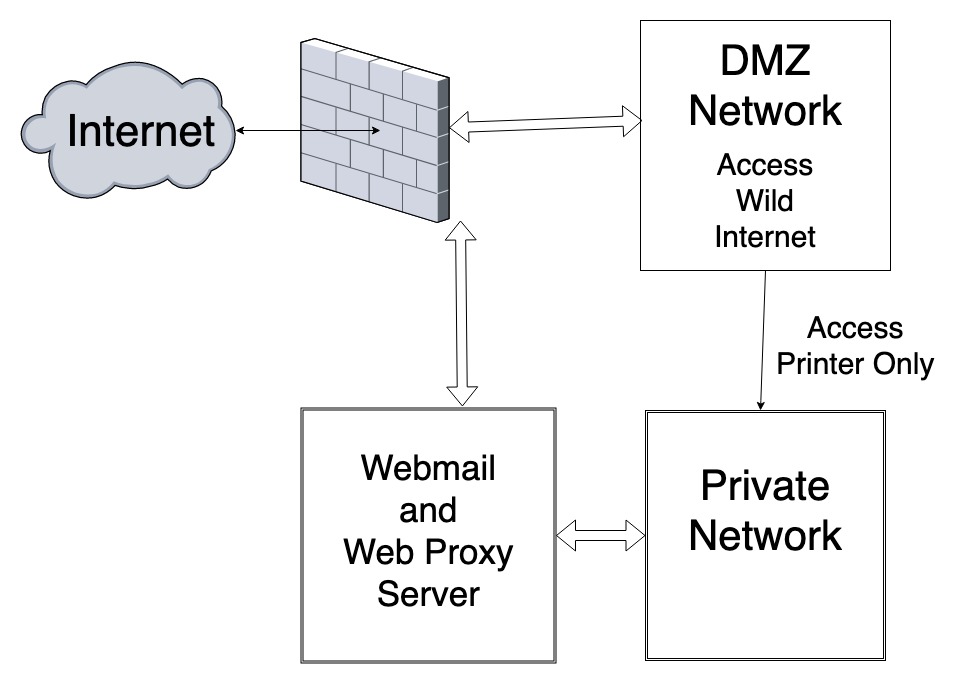
At a very-high level, the network design connects to the Internet (e.g., to your Internet Modem) only through a Firewall. The Firewall is actually a computer; that is true whether you are using a “Firewall Appliance” or a Linux Server. A Linux Server is just a Hardware PC with additional network ports that primarily routes network traffic.
The Operating System on the Linux Server is one of several versions of Linux, which is a free and open source general purpose operating system. The version I recommend is Ubuntu Server LTS. Ubuntu versions are labeled by year and month released, and the LTS means “Long Term Support,” which for the Server versions of Ubuntu means that Ubuntu promises to provide security updates for five years. Ubuntu releases a Server LTS version in April every two years, so Ubuntu Server 18.04 LTS is released in April, 2018, and Ubuntu Server 20.04 LTS is released in April, 2020.
Private Network
The “Private Network” in the diagram above is the main office network used by employees to access EMR and Patient Management software. Access to and from this network must be carefully restricted. If there is a Wifi Access Point on this network, it must have a good WPA2 password, and only used with the few trusted devices that need access to the EMR and Patient Management software, and it should NOT be provided to employees to use on their personal phones, etc. Similarly, there must not be any jacks or other connectors in reception areas or other locations that could be accessed by unauthorized persons.
The Firewall is configured to prevent both INBOUND and OUTBOUND access to the Internet from the Private Network. This is one of the most common security flaws of Office Networks.
Because they do not have outbound access to the Internet, the computers on the Private Network cannot directly browse the Internet or access Webmail or other mail servers. Thus, the Firewall prevents email attachments and malicious websites from being accessed from the Private Network.
Webmail And Web Proxy Server
If there are some specific trusted websites and/or email without attachments that should be accessible from within the Private Network, a Webmail and/or Web Proxy Server can be used. This is another computer, accessible from within the Private Network that itself has access to the Internet through the Firewall.
As a Webmail Server, it runs a modified version of Webmail software, such as open-source Roundcube, which allows staff to view and send emails hosted on an external IMAP mail server, but which does not allow attachments to be viewed and/or downloaded. If staff needs access to attachments in an email, the same IMAP server can be accessed from another computer that does have unrestricted Internet access, such as within the DMZ Network.
As a Web Proxy Server, it runs software such as open-source Squid, which accepts connections from browsers within the Private Network, and itself accesses the websites on the Internet, passing the information from those sites to the Private Network browsers. However, the Proxy Server only allows access to the few trusted websites that should be accessible from within the Private Network. These sites are included in a Whitelist on the Web Proxy Server.
It is very important NOT to include general purpose sites, such as Google, Gmail, or any webmail sites on the Whitelist, because that would circumvent the prevention of attachments on the Private Network.
DMZ Network – Access the Wild Internet
If there is a need for staff to access the Internet to browse, view email attachments, etc., you can set up a “DMZ” network, which has some components of both the outside Internet and the inside Private Network.
Computers on the DMZ network can access any site on the Internet, and thus are vulnerable to all of the security risks that entails, such as Ransomware, etc. However, these computers have no access to the Private Network or any important personal information.
If these computers need to print, either a dedicated printer on the DMZ network can be used, or else, the Firewall can be configured to allow computers on the DMZ network to connect only to the printer on the Private Network.